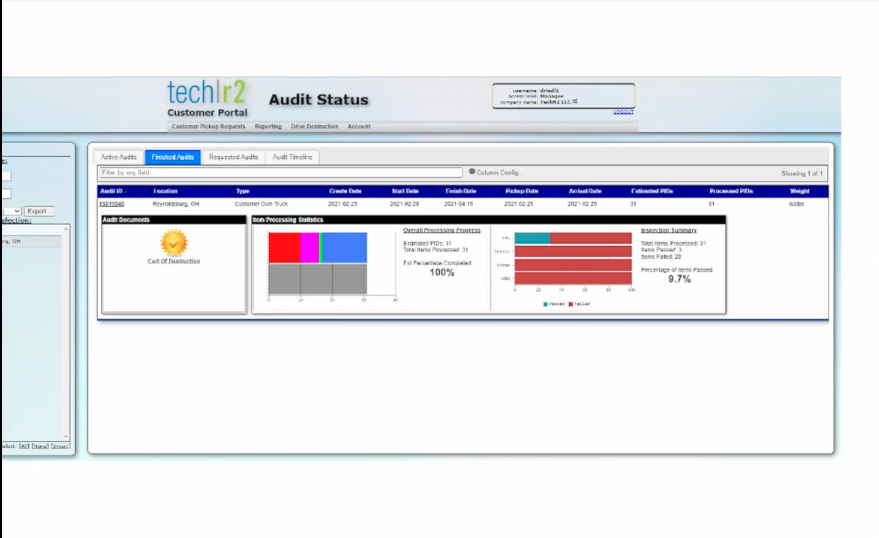
[vc_row type=”grid” video_bg=””][vc_column width=”2/3″ dp_animation=””][vc_column_text dp_animation=””]
TechR2’s Tear-A-Byte and Tear-A-Vault Systems meet the Zero Trust Security Model.
[/vc_column_text][/vc_column][vc_column width=”1/3″ dp_animation=””][/vc_column][/vc_row][vc_row type=”grid” video_bg=””][vc_column width=”1/3″ dp_animation=””][vc_column_text dp_animation=””]From Charles Robbins[/vc_column_text][space size=”30″][vc_single_image image=”15625″ img_size=”full” alignment=”center” dp_animation=””][/vc_column][vc_column width=”1/3″ dp_animation=””][vc_column_text dp_animation=””]August 24, 2021
Every day we work within our organization to help clients achieve requirements in a CSF standard they thought was unattainable. As being discussed at the cybersecurity summit in Washington DC today is that there is a shortage of cyber expertise. True. But what can we do locally to correct the issue? Two things. One, your partners that supply your technology need to be embedded in the CSF process by regular audits and proven certifications. That will thin the partners list down pass the halfway mark as most OEMs and IT support utilize non-compliant third-party vendors in their Supply Chain. Next, we start to train a diverse team of individuals at our organization in cybersecurity using the NIST CSF as our guideline.[/vc_column_text][/vc_column][vc_column width=”1/3″ dp_animation=””][vc_column_text dp_animation=””]When you incorporate the Zero Trust Security Model in your planning, every effort forward will result in user sign on using MFA and with the least privileges being granted. Department personnel can help identify user accounts to be deactivated, endpoint devices that should not allow access and way too much free contact to the open Internet. When people learn at work, they can practice their cyber hygiene at home. Therefore, you can do two things to start today, compliant partners, and CSF training that results in proactive change. These steps will help your business and the US cyber defense.[/vc_column_text][vc_separator css=”.vc_custom_1629903638689{padding-top: 18px !important;padding-bottom: 24px !important;}”][vc_column_text dp_animation=””]Related article: Apple, Google, Amazon CEOs will head to White House today for cybersecurity meeting – CNET
[/vc_column_text][vc_empty_space][vc_column_text dp_animation=””]
TechR2’s Tear-A-Byte and Tear-A-Vault Systems meet the Zero Trust Security Model. This new national cybersecurity model that meets the NIST CSF requirements.
[/vc_column_text][/vc_column][/vc_row][vc_row type=”grid” video_bg=””][vc_column dp_animation=””][vc_separator][/vc_column][/vc_row][vc_row type=”grid” video_bg=””][vc_column width=”1/2″ dp_animation=””][vc_widget_sidebar sidebar_id=”posts-footer-block-left”][/vc_column][vc_column width=”1/2″ dp_animation=””][vc_widget_sidebar sidebar_id=”posts-footer-block-right”][/vc_column][/vc_row]