Tear-A-Byte®, The patented exclusive onsite data eradication solution by TechR2
Do you know where your hard drives go at night?
The #1 cause of large-scale data breaches is the loss of data-bearing media.
Data breaches have become a major concern in every business and industry, from healthcare to education, banking to retail, costing a company $5 million on average. Privacy Rights Clearinghouse reported more than 678 data breaches in 2012, involving 27.4 million records (that’s more than the population of the entire state of Texas!).
Don’t let your organization become a statistic, allow TechR2 to assist in mitigating your risk with our Tear-A-Byte® process.
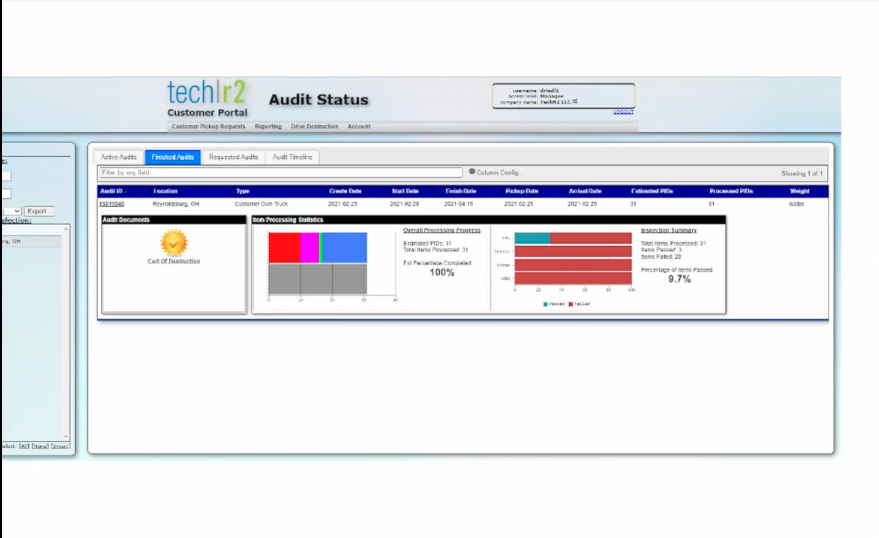
Cost-effective and easy to implement, the Tear-A-Byte® solution ensures compliance with all data security regulations. Customized to fit the needs of your enterprise, in some cases it can be as simple as placing a barcode (PID) sticker on your hard drives and dropping them into a secure container. Once the container is at capacity our technicians will come to you to perform the secure data destruction service. For a higher level of security, the client will scan their inventory into our secure customer portal. This allows the client to capture the unique attributes of each hard drive prior to placing the drives in a secure container. To continue learning about our services, view the image below and visit our detailed process page. Tear-A-Byte® utilizes state-of-the-art technology to provide secure onsite data destruction with our National Security Agency certified degausser.
Contact TechR2 today to request a trial or Tear-A-Byte® demo. We will mitigate your risk of a data breach that could lead to significant fines, litigation, and most of all – harm to your brand’s reputation.
Additional features of the Tear-A-Byte® solution include:
- Secure onsite destruction to NIST800-88 specifications using certified people, processes and technologies.
- Disk Security Containment Solutions confine and secure devices awaiting destruction.
- Cloud-based application, which allows the client to create an inventory of devices and record their unique attributes.
- Compliance with HIPAA, HITECH, PCI, SOX, GLBA, etc.
- Safeguards corporate sustainability through simple, but comprehensive measures.
[vc_row type=”grid” row_type=”section” bg_image_repeat=”repeat” padding_top=”24″ padding_bottom=”24″][vc_column dp_animation=””][vc_separator][/vc_column][/vc_row][vc_row type=”grid” video_bg=””][vc_column width=”1/2″ dp_animation=””][vc_widget_sidebar sidebar_id=”posts-footer-block-left”][/vc_column][vc_column width=”1/2″ dp_animation=””][vc_widget_sidebar sidebar_id=”posts-footer-block-right”][/vc_column][/vc_row]