We Track>Contain>Destroy>VerifyYour Data Bearing devices within the four walls of your organization
At TechR2, we eradicate data on failed hard drives and other retired IT devices.
Our patented systems for securely and thoroughly destroying data from hard drives, laptops, and any other data-bearing devices can ensure your organization is fully compliant with all data-security and environmental regulations.
Introducing Tear-A-Byte
The Most Secure and Compliant Solution Available
The patented Tear-A-Byte appliance and process exists for one reason: To fully protect you from data breaches related to mismanaged failed or retired drives in your datacenter.
No other solution offers a more secure, compliant, or easy way to Track, Contain, Destroy, and Verify the destruction of hard drives.
Data is the DNA of Your Business
Your data defines who you are as a business. What you take in and generate is unique to you and you alone.
Is your data safe? Who among your competitors wouldn’t love the opportunity to dive into your business’s DNA and find out what secrets it can unlock? What might they find? Customer data? Financial records? One loose data bearing device can divulge everything and send your business into a PR nightmare. Without a bullet proof plan and solid implementation, it is only a matter of time before a loose data-bearing device finds its way into the hands of a bad actor.
TechR2 is the only company in the industry that has been awarded a US Patent for its Track-Contain-Destroy-Verify data security process, is OEM approved, upholds critical ISO certifications, and is recognized for compliance with GDPR, NIST and all governmental regulations concerning data destruction, including ISO 27001, ISO 14001, ISO 9001, and ISO 45001.

Security Services
Lorem ipsum dolor sit amet, consect adipiscing elit, sed do eiusmod tempor incididunt ut labore

Data Privacy
Lorem ipsum dolor sit amet, consect adipiscing elit, sed do eiusmod tempor incididunt ut labore

Industry Certified
Lorem ipsum dolor sit amet, consect adipiscing elit, sed do eiusmod tempor incididunt ut labore
ITAD Is Dead!
ITAD vendors can READ your customer data during the overwrite process!
Today, because of GDPR, NIST, ZTA, CCPA and IRS 1075, cybersecurity assessors from the government GAO, IRS, DoD, NERC, PCI, HIPAA or more will examine you, your contractors, and all of their subcontractors. It is your responsibility to verify compliance of your entire supply chain and ignore the supplier’s embellishments of a fictitious data governance.
The old ITAD system no longer upholds all cybersecurity requirements and can be rendered obsolete (dead).
What Has Changed in Data Control?
- The Data Destruction process must meet your Risk Assessment requirements
- Data Destruction must occur under your control per Federal, State and Industry regulations
- Vendor must be Cybersecurity Framework certified per Federal, State and Industry regulations… and more
Webinar Series
Learn how to protect the data on your end-of-life IT devices.
Join a conversation with our Chief Compliance Officer
and learn how partnering with TechR2 can keep your
data secure and your organization compliant.

Risk Assessment

Effective Compliance
Our ISO Certifications






No IT Asset Management Company has Earned More Certifications and Patents than TechR2.
Peace of Mind Compliance
Total Data Eradication Services
From decommissioning an entire datacenter, to securely destroying the data on a few dozen laptops each week…
From degaussing or shredding drives, to providing secure transport of data-bearing devices…
With over a dozen federal and international organizations developing and enforcing data-security and environmental regulations regarding retired drives and IT devices, it can be nearly impossible for most companies to keep up with it all.
At TechR2, all our products and services are designed, built, and executed to keep you fully compliant with all US and EU regulations for all your end-of-life IT equipment.
Cybersecurity Projects
Clients Protection
Service Guarantee
Team Experts
Case Studies
Proven Relationships and Experience

Data Centers
Datacenter Decommissioning for Leading Telecommunications Company

Hard Drives
Track, Contain, Destroy, and Verify Technique to Secure Data on Failed Hard Drives for Major International Airline

End-of-Life Assets
End-of-Life IT Asset Management and Data Eradication for National Fragrance and Body Care Retailer.
The number one cause of large-scale data breaches is data-bearing devices ending up in the hands of the wrong people.
Whether it’s a failed hard drive or a retired laptop, data-bearing devices ending up in the hands of the wrong people can lead to issues beyond simply the data on that device (which is bad enough). Cyber criminals can also use the information on those devices to infiltrate your systems. And that’s when things can get really serious.
Data Eradication News & Insights
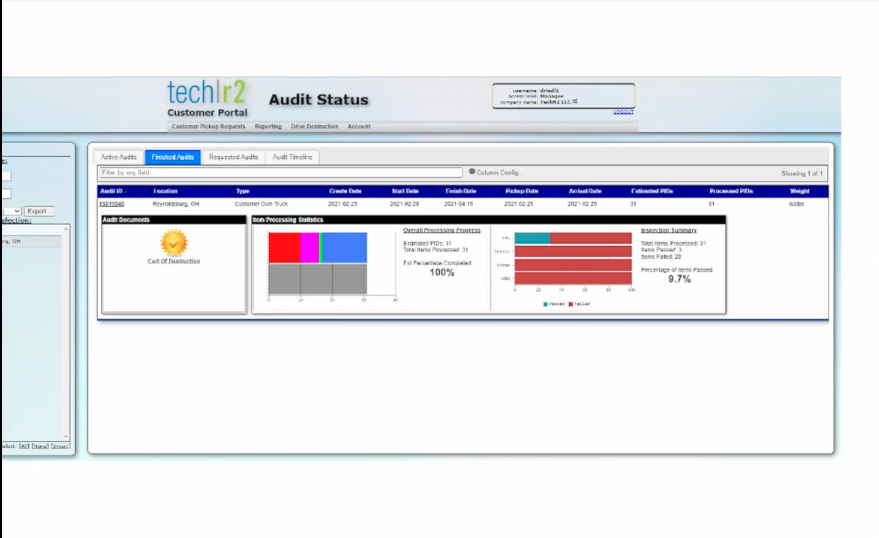
The Customer Portal: Audit Status, Inventory Reporting, Certificates of Destruction, Green Reports
The Customer Portal: Audit Status, Inventory Reporting, Certificates of Destruction, Green Reports
A look at the Tear-A-Byte and the Tear-A-Vault
Are your failed data-bearing devices protected after decommission? We’ve earned worldwide trust in keeping enterprises safe from brand compromise.